Fine-Tuning Performance for Digital Excellence.

At iAssureIT, we prioritize the integrity and security of your digital platforms. Rooted in extensive threat analysis and state-of-the-art methodologies, our mission is to protect your business assets from potential vulnerabilities. We are more than testers; we are your guardians in the digital realm.
- Proactive security testing solutions that protect, detect, and respond to threats.
- Our security specialists employ an in-depth vulnerability assessment approach.
- Boasting a team of 150+ seasoned professionals geared to safeguard your digital landscape.
- An impressive record of 200+ successful security testing projects, ever-adapting to the swiftly changing threat environment.
Advancing Security
Protecting Integrity
Proactive security testing solutions that protect, detect, and respond to threats.
Our security specialists employ an in-depth vulnerability assessment approach.

Boasting a team of 150+ seasoned professionals geared to safeguard your digital landscape.
An impressive record of 200+ successful security testing projects, ever-adapting to the swiftly changing threat environment.
Security Challenges Businesses Face : iAssure Security Solutions

PROBLEM
Evolving Cyber Threats :
Combatting the continuous evolution of cyber threats.
iAssureIT Solution
Through comprehensive penetration testing, we expose potential weaknesses and fortify defenses, ensuring robust protection against emerging threats.


Fortify your Digital Assets and instill trust among stakeholders.
Request a Quote +919270003690
Request a Quote +919270003690

PROBLEM
Protecting Sensitive Data :
Ensuring the safety of sensitive customer and business data.
iAssureIT Solution
Our data-centric security approach emphasizes encrypting, monitoring, and safe guarding critical information against breaches.

Uncover Vulnerabilities with Our Comprehensive Security Testing Services.

Let iAssureIT be your bulwark against cyber threats.
Let's Safeguard Digital Assets Together!
Let's Safeguard Digital Assets Together!
Our Premier Security Testing Services

Threat Analysis
A systematic review to identify and prioritize potential threats, forming the groundwork for robust defense strategies.

Vulnerability Assessment
Detailed evaluations of your systems to spot weaknesses before malicious entities do.

Penetration Testing
Simulated cyber-attacks to test the strength of your digital defenses, ensuring they stand tall against real-world threats.

Intrusion Detection
Real-time monitoring for any unauthorized activities, enabling swift response actions.

Secure Code Review
Ensuring the software code is free from vulnerabilities and adheres to security best practices.

Continuous Monitoring
With threats ever-evolving, we remain vigilant, offering 24/7 monitoring to safeguard your assets.

Compliance and Standards
Ensuring your platforms comply with international security standards and regulatory requirements.
NATIONAL AWARDS
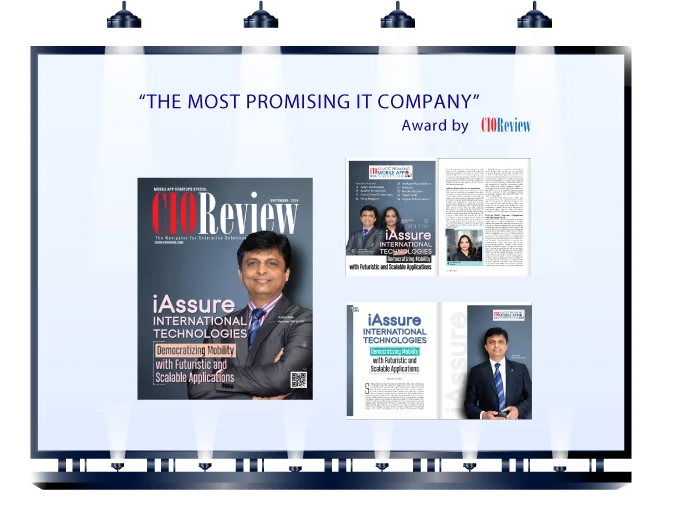
1. The Company Of The Year 2018
The prestigious award of ' The Company of The Year - 2018' in Startup Category for Web & Mobile Application Development from International Magazine CIO Review.
Read More

Let iAssureIT be your bulwark against cyber threats.
Let's Safeguard Digital Assets Together!
Let's Safeguard Digital Assets Together!
CASE STUDIES
We shed light on our work and what goes behind the development

Coffic-1

BCI (Better Cotton Initiative)

LYVO

Unimandai
Five Bees

Pipito
WHY CHOOSE IASSUREIT FOR
Robust Security Testing?


Expertise
A dedicated team of security experts, always on the front lines of cybersecurity evolution.

Quality Assurance
igorous testing to ensure your defenses are both resilient and adaptive.

Custom Solutions
Personalized security protocols aligned with your specific business requirements and threat landscape.

Continuous Support
An ongoing partnership, always adapting and fortifying defenses in light of new challenges.

Take the proactive step towards robust cybersecurity. Learn more about our top-tier Security Testing services.
Contact us today +919270003690
Contact us today +919270003690
FAQS
+
Why is Security Testing vital?
+
What differentiates iAssureIT's Security Testing approach?
+
How does iAssureIT handle Vulnerability Assessments?
+
What is the value of Penetration Testing?
+
How does Continuous Monitoring enhance security?
+
What compliance standards does iAssureIT adhere to?
+
How can I get started with iAssureIT’s Security Testing Services?
CONTACT US
Now why to wait?
Contact Us immediately
Contact Us immediately


Our Awards
TOP 50 BRAND FUTURE
COMPANY OF THE YEAR 2018
THE MOST PROMISING IT COMPANY OF 2018
THE MOST INNOVATIVE IT COMPANY 2019
Copyright © 2025, iAssureIT All Rights Reserved
Privacy Policy